Every day, a large flow of transport runs in the territories of warehouses, factories, terminals and other high-security facilities, among which there may be trucks entering for loading and unloading raw materials, cars of employees, customers and others. At the same time, the entire burden associated with the control and registration of vehicles entering the enterprise falls on a limited number of checkpoints.
In such conditions, checkpoints with manual data processing often fail to cope with their tasks, due to which the logistics in the enterprise can be disrupted, and the security of the facilities is correspondingly reduced. Therefore, companies are increasingly giving preference to ACS – automated transport access control and management systems that perform several important tasks at once:
Thanks to automation, the throughput of checkpoints is significantly increased and, at the same time, errors on the part of personnel due to the human factor, as well as their negative impact on processes, are eliminated.
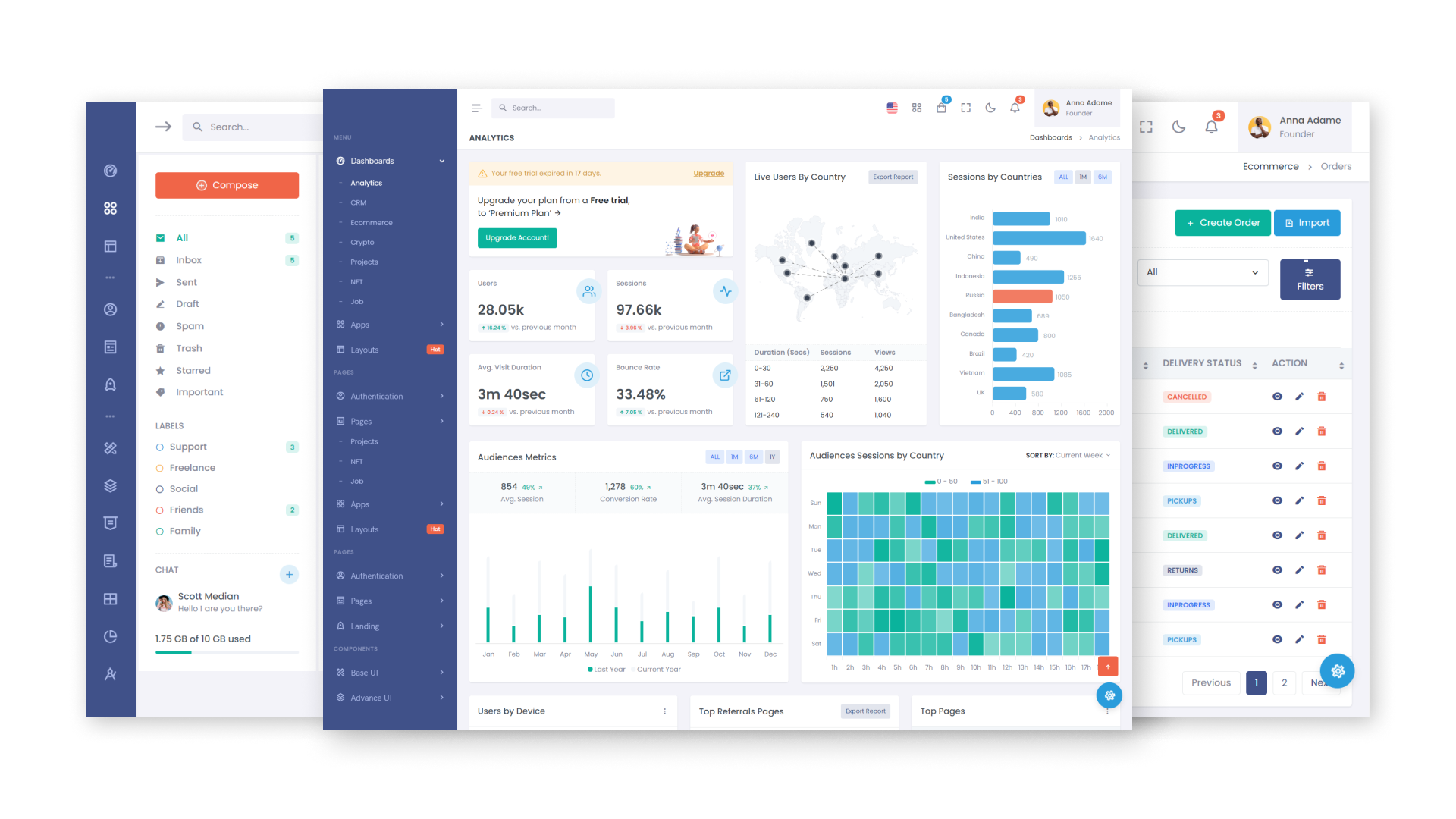
The vehicle access control and management system captures a vehicle approaching the checkpoint using a video camera and sends the data to the server, where the vehicle is identified and its number is checked against the database. If information about the car is found and it has the right to enter the territory of the facility, a signal is automatically given to open the barrier and the fact of the entry of the vehicle is recorded.
If the vehicle data was not found on the server, an alarm event is automatically created, and its entry into the territory of the enterprise is prohibited. At the same time, the operator can carry out a manual check of the car and ensure the passage in manual mode, if necessary, as well as enter information about it into the database.
In addition, in the process of implementing the ACS system, there is the possibility of additional verification of vehicles in appearance. In this case, the picture of the vehicle from the video camera will be compared with its photo in the database, which will eliminate the possibility of license plate spoofing.
It is also worth noting that access control systems are developed taking into account the individual needs of each particular company, so their functionality and capabilities may vary.
ACS systems include a whole range of software solutions that function as a single mechanism through the use of a single and centralized database. Therefore, different technologies can be involved in the development of such projects:
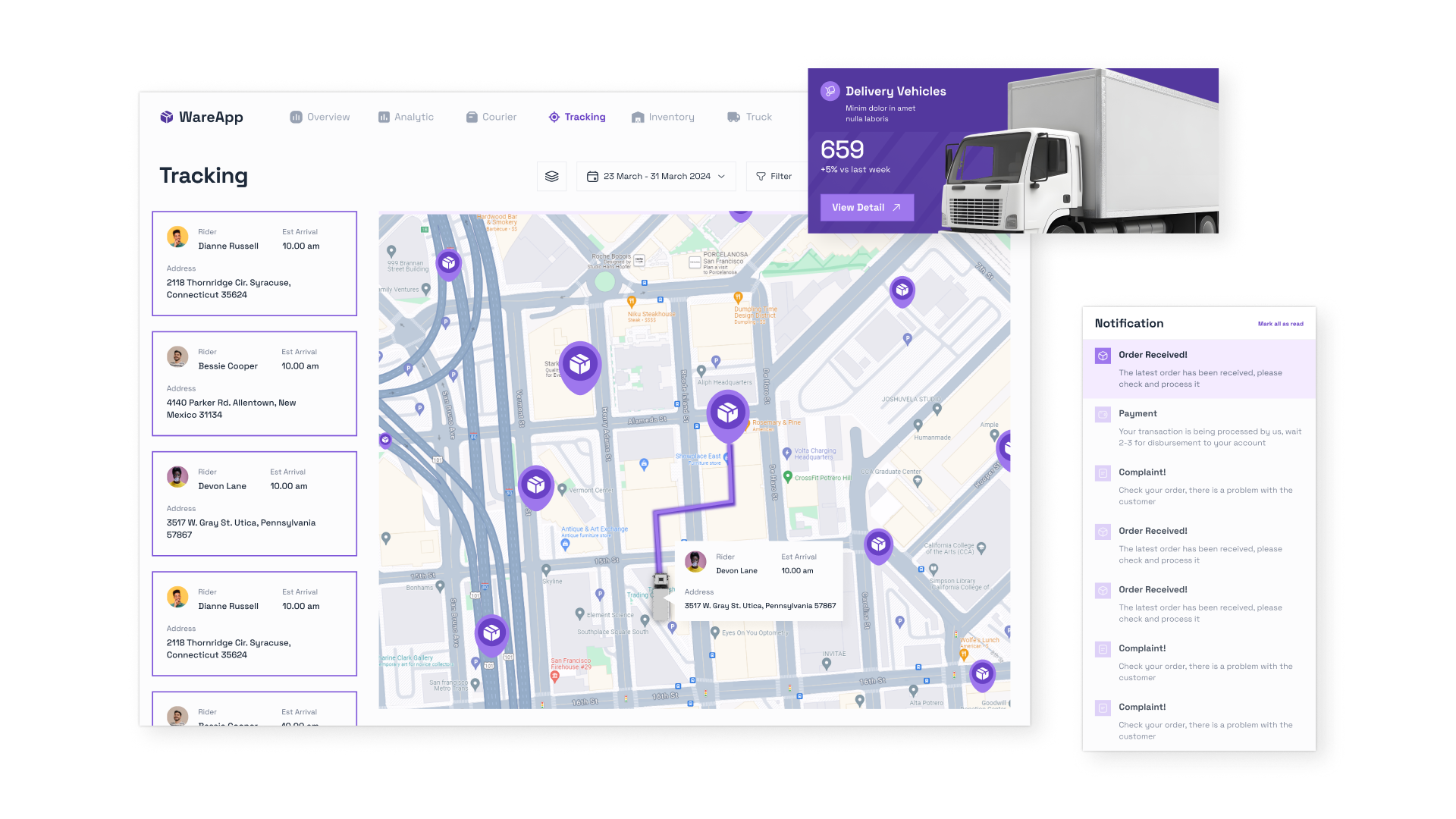
The development and launch of access control systems for transport may seem quite complicated, because many things need to be foreseen: what parts the project will consist of, how information about the car will be read and checked, how operators will interact with the interface and what features they need for efficient work. Large tasks are best solved by breaking them down into small steps, so let’s consider what stages the development of such systems consists of.
Stage 1. Gathering information
Conducting preliminary research is already commonplace when creating any digital product. At this stage, specialists will have to find out how the process of passing transport at the enterprise is built, who controls it and how to automate it as efficiently as possible.
To do this, meetings are held with a representative of the customer and the current IT infrastructure of the company is analyzed.
Stage 2. Development of technical documentation and design
When the data is collected, and the goals and objectives are set, the specialists proceed to the formation of technical documentation. This is a kind of foundation for the project, which describes in detail: the technology stack, functionality, interface structure, the logic of interaction between different constituent elements and the implementation plan.
As a result, we will get a carefully thought-out mockup of the ACS system, which will be used as the basis for all subsequent stages.
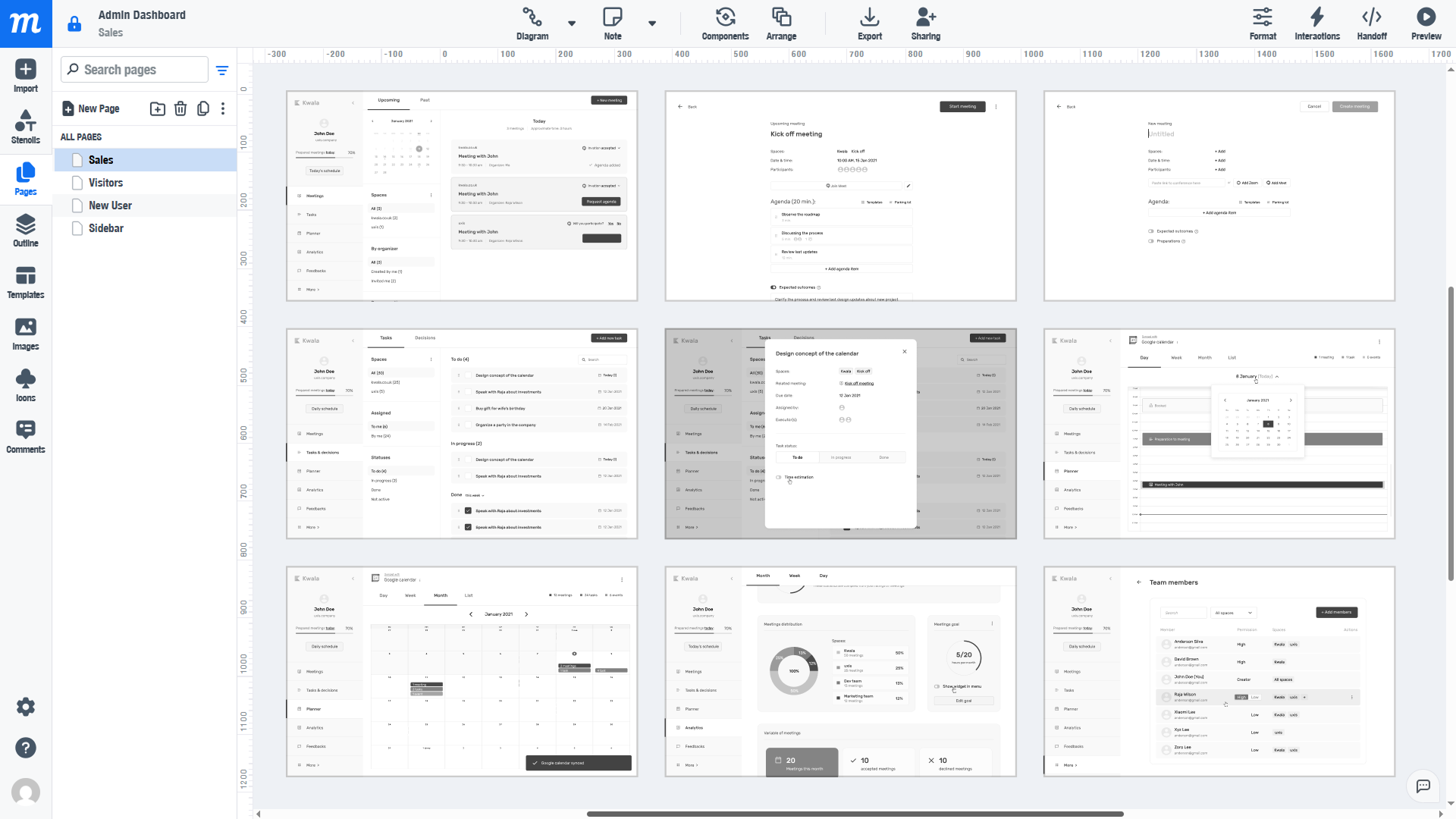
Stage 3. Design
For an ACS system, an intuitive interface is no less important than functionality. At least it depends on him how convenient it will be for operators to work with the new software and how much time it will take to train them.
To create a comfortable and logical interface, professional UI designers are involved in the project. They can develop a design completely from scratch, or using existing patterns and templates, which significantly speeds up production.
Stage 4. Creation of the software part
Programming the functionality for the transport access control and management system is the most time-consuming stage, which consists of two parts:
Stage 5. Testing
After the technical development is completed, the transport access control system goes through several levels of testing. This allows you to identify most of the possible errors even before the project is put into operation. Main types of testing:
At the last stage, the compliance of the project with the initial plans and requirements of the customer, as well as its ability to fulfill the tasks assigned to it, is checked.
Stage 6. Support and development
When the testing is completed, the ACS is deployed on the company’s devices, and the staff is trained to work with the new software. However, at this stage, the technical work on the project is still not completed.
The fact is that after the start of using the system in real conditions, users may encounter hidden errors that were not detected at the previous stages and need to be eliminated. In this case, the developers quickly determine the cause of the problem and perform the necessary improvements.
In addition, the first months of using the ACS system often show what functionality is missing and what can be improved to increase its efficiency. Such work is carried out by specialists as part of the development of the project by releasing patches with updates and installing them into a functioning system.
The ACS system increases the throughput of the checkpoint and automates most of the processes associated with the control of passing vehicles. With its help, you can organize more efficient logistics, which, accordingly, will lead to an increase in the profitability of the entire business.
Our company has practical experience in the implementation and deployment of access control systems in the territories of various facilities. For the development of such projects, we use already formed teams of specialists with well-established communication, thanks to which we can guarantee the high quality of the software being created.
Our works
Contact the experts Have a question?
The user, filling out an application on the website https://avada-media.ua/ (hereinafter referred to as the Site), agrees to the terms of this Consent for the processing of personal data (hereinafter referred to as the Consent) in accordance with the Law of Ukraine “On the collection of personal data”. Acceptance of the offer of the Consent is the sending of an application from the Site or an order from the Operator by telephone of the Site.
The user gives his consent to the processing of his personal data with the following conditions:
1. This Consent is given to the processing of personal data both without and using automation tools.
2. Consent applies to the following information: name, phone, email.
3. Consent to the processing of personal data is given in order to provide the User with an answer to the application, further conclude and fulfill obligations under the contracts, provide customer support, inform about services that, in the opinion of the Operator, may be of interest to the User, conduct surveys and market research.
4. The User grants the Operator the right to carry out the following actions (operations) with personal data: collection, recording, systematization, accumulation, storage, clarification (updating, changing), use, depersonalization, blocking, deletion and destruction, transfer to third parties, with the consent of the subject of personal data and compliance with measures to protect personal data from unauthorized access.
5. Personal data is processed by the Operator until all necessary procedures are completed. Also, processing can be stopped at the request of the User by e-mail: info@avada-media.com.ua
6. The User confirms that by giving Consent, he acts freely, by his will and in his interest.
7. This Consent is valid indefinitely until the termination of the processing of personal data for the reasons specified in clause 5 of this document.
Send CV
Contact us in any convenient way for you:
+ 38 (097) 036 29 32